
Embark on a journey into the world of computer security certifications for IT professionals, where opportunities for career growth and success await those who dare to take on the challenge. From exploring the importance of certifications to unveiling the benefits of career advancement, this topic promises to be both enlightening and exciting.
As we delve deeper into the realm of computer security certifications, you’ll discover a wealth of information that will empower you to make informed decisions about your professional development.
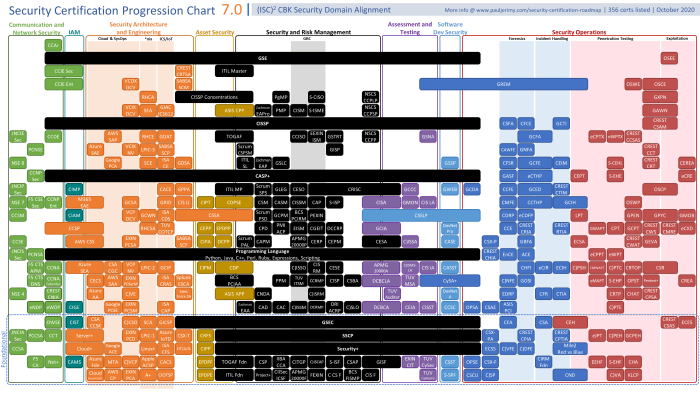
Computer Security Certifications for IT Professionals
Computer security certifications are essential in the IT industry as they validate a professional’s skills and knowledge in safeguarding computer systems and networks from cyber threats. These certifications demonstrate expertise in areas such as ethical hacking, network security, and information security management.
Popular Computer Security Certification Programs
- CompTIA Security+: A foundational certification covering network security, compliance, and operational security.
- Certified Information Systems Security Professional (CISSP): A globally recognized certification focusing on security architecture, design, and management.
- Certified Ethical Hacker (CEH): Specifically designed for professionals who want to specialize in ethical hacking and penetration testing.
Benefits of Computer Security Certifications for Career Advancement
Having computer security certifications can open up new career opportunities and increase earning potential. Employers value certified professionals who can protect their organizations from cyber threats, making them more marketable in the industry.
Comparison of Different Levels of Computer Security Certifications
- Entry-Level Certifications: These certifications, such as CompTIA Security+, are suitable for beginners and require foundational knowledge of computer security.
- Mid-Level Certifications: Certifications like CISSP cater to experienced professionals looking to advance their careers in security management and architecture.
- Specialized Certifications: Certifications like CEH focus on specific areas like ethical hacking and penetration testing, offering in-depth knowledge and expertise in niche fields.
Mobile Computing
Mobile computing plays a crucial role in today’s technological landscape, allowing users to access information and services on the go. With the increasing popularity of smartphones, tablets, and other portable devices, mobile computing has become an integral part of our daily lives.
Significance of Mobile Computing
- Facilitates remote work and collaboration
- Enables real-time access to data and applications
- Enhances productivity and efficiency
Challenges and Security Considerations
- Device theft and loss pose a risk to sensitive data
- Insecure Wi-Fi networks can lead to unauthorized access
- Malware and phishing attacks target mobile devices
Popular Mobile Computing Devices and Operating Systems
- Devices: iPhone, Samsung Galaxy, iPad, Google Pixel
- Operating Systems: iOS, Android, Windows Mobile
Impact on IT Professionals’ Roles and Responsibilities
- Need to secure mobile devices and networks
- Implementing mobile device management solutions
- Adapting security policies for mobile workforce
Computer Programming
Computer programming skills are crucial for IT professionals as they allow individuals to create, modify, and optimize software applications, websites, and systems. Programming knowledge enables professionals to solve complex problems, automate tasks, and improve efficiency in various IT projects.
Comparison of Programming Languages
- Java: Known for its portability and versatility, Java is widely used in enterprise applications and mobile development.
- Python: Recognized for its simplicity and readability, Python is often used in data science, artificial intelligence, and web development.
- C++: Ideal for system programming and developing high-performance applications, C++ is commonly used in game development and operating systems.
- JavaScript: Essential for web development, JavaScript is used for creating interactive websites and web applications.
Role of Programming in Cybersecurity
Programming plays a crucial role in enhancing cybersecurity measures by enabling professionals to develop secure applications, implement encryption algorithms, and build robust defense mechanisms against cyber threats. By writing secure code and performing penetration testing, programmers can identify vulnerabilities and mitigate risks effectively.
Real-world Applications of Computer Programming
- Cryptocurrency: Programming skills are essential for developing blockchain technology and securing transactions in cryptocurrencies like Bitcoin.
- Healthcare Systems: Programmers use their skills to create software for managing patient records, ensuring data privacy and security in healthcare environments.
- Autonomous Vehicles: Programming is vital for designing algorithms that enable self-driving cars to navigate safely and make real-time decisions on the road.
Computer Security
Computer security is a critical aspect of IT infrastructure that focuses on protecting data, networks, and systems from unauthorized access, cyberattacks, and data breaches. It encompasses various principles and practices to ensure the confidentiality, integrity, and availability of information.
Key Principles of Computer Security and Their Significance
- Authentication: Verifying the identity of users and systems to prevent unauthorized access.
- Authorization: Granting appropriate access rights to users based on their roles and responsibilities.
- Encryption: Converting data into a secure format to prevent unauthorized interception.
- Firewalls: Implementing barriers to filter network traffic and block malicious activities.
Common Cybersecurity Threats and Mitigation Strategies
- Malware: Software designed to disrupt, damage, or gain unauthorized access to systems. Mitigation includes regular software updates and antivirus protection.
- Phishing: Deceptive emails or websites used to trick users into revealing sensitive information. Education and awareness training help mitigate this threat.
- DDoS Attacks: Overwhelming a network with excessive traffic to disrupt services. Mitigation involves implementing DDoS protection solutions and monitoring network traffic.
Role of Encryption in Ensuring Computer Security
Encryption plays a crucial role in safeguarding sensitive data by converting it into a secure format that can only be decrypted with the right keys. It ensures confidentiality and integrity during data transmission and storage.
Best Practices for Maintaining Computer Security in Organizations
- Regular Security Audits: Conducting assessments to identify vulnerabilities and weaknesses in the system.
- Employee Training: Educating staff on cybersecurity best practices to prevent human errors and ensure data protection.
- Access Control: Implementing strong authentication mechanisms and limiting access based on the principle of least privilege.
- Data Backup: Regularly backing up critical data to recover in case of ransomware attacks or data loss incidents.
Computer Software
Software plays a crucial role in the field of IT, serving as the foundation for various applications and systems that power modern technology. It encompasses a wide range of programs, applications, and operating systems that enable computers to perform specific tasks and functions efficiently.
Types of Computer Software
- Operating Systems: Examples include Windows, macOS, and Linux, which manage computer hardware and provide a platform for running applications.
- Applications Software: Includes programs like Microsoft Office, Adobe Photoshop, and web browsers, designed for specific tasks or functions.
- Programming Software: Tools such as IDEs (Integrated Development Environments) like Visual Studio and Eclipse, used by developers to write, test, and debug code.
- Security Software: Programs like antivirus software, firewalls, and encryption tools that protect systems from cyber threats.
Role of Software Updates in Security
Regular software updates are essential for enhancing security measures in IT systems. Updates often include patches to fix vulnerabilities and bugs that could be exploited by cyber attackers. By keeping software up-to-date, IT professionals can minimize the risk of security breaches and ensure the protection of sensitive data.
Popular Security Software Tools
- Antivirus Software: Examples include Norton, McAfee, and Bitdefender, which detect and remove malware from systems.
- Firewalls: Tools like Windows Firewall and pfSense help monitor and control incoming and outgoing network traffic to prevent unauthorized access.
- Encryption Software: Programs like VeraCrypt and BitLocker encrypt data to protect it from unauthorized access or theft.
Computer Systems

Computer systems are essential for processing, storing, and managing data in various industries. These systems consist of hardware components like the central processing unit (CPU), memory, storage devices, and input/output devices, as well as software components such as operating systems and applications.
Components of Computer Systems and Their Functions
- The Central Processing Unit (CPU): The brain of the computer that executes instructions and processes data.
- Memory (RAM): Temporary storage for data and instructions currently in use by the CPU.
- Storage Devices (Hard Drive, SSD): Long-term storage for data and programs.
- Input/Output Devices (Keyboard, Mouse, Monitor): Allow users to interact with the computer system.
Importance of System Architecture
System architecture plays a crucial role in determining how efficiently a computer system functions. A well-designed architecture can optimize performance, scalability, and reliability.
Types of Computer Systems
- Mainframes: Powerful systems used for large-scale computing tasks in organizations like banks and government agencies.
- Servers: Computers dedicated to providing services or resources to other computers on a network.
- Personal Computers: Individual desktops, laptops, or workstations used by individuals for personal or professional tasks.
Operating Systems
- Windows: Developed by Microsoft, widely used in personal computers and servers.
- macOS: Operating system for Apple computers and laptops.
- Linux: Open-source operating system popular for servers and technical applications.
Ending Remarks
In conclusion, computer security certifications for IT professionals offer a pathway to success in the ever-evolving landscape of technology. By arming yourself with the right certifications, you can position yourself for growth, success, and a fulfilling career in the IT industry.
Commonly Asked Questions
What are the most popular computer security certification programs?
Some of the top computer security certification programs include CISSP, CEH, CompTIA Security+, and CISM.
How do computer security certifications benefit career advancement?
Computer security certifications validate your expertise, enhance credibility, open doors to better job opportunities, and often lead to higher salaries.
What are the different levels of computer security certifications?
Common levels include entry-level, associate, professional, expert, and architect certifications, each requiring varying levels of experience and expertise.





