
Step into the world of Cloud computing systems for businesses where innovation meets practicality. From optimizing resources to ensuring data security, this overview promises to unravel the complexities of cloud technology in a fun and interactive way.
Get ready to explore the realm of cloud computing models, best practices, and mobile integration that are revolutionizing the way businesses operate in the digital age.
Overview of Cloud Computing Systems for Businesses
Cloud computing has revolutionized the way businesses operate by providing access to a shared pool of resources and services over the internet. Instead of investing in costly hardware and infrastructure, businesses can now leverage cloud computing systems to store data, run applications, and streamline operations.
Benefits of Using Cloud Computing Systems
- Cost-Efficiency: Businesses can save money by only paying for the resources they use, eliminating the need for upfront investments in hardware.
- Scalability: Cloud computing systems allow businesses to easily scale up or down based on their needs, ensuring flexibility and agility.
- Accessibility: With cloud computing, employees can access data and applications from anywhere, promoting collaboration and remote work.
- Data Security: Cloud providers offer robust security measures to protect sensitive business data, reducing the risk of data breaches.
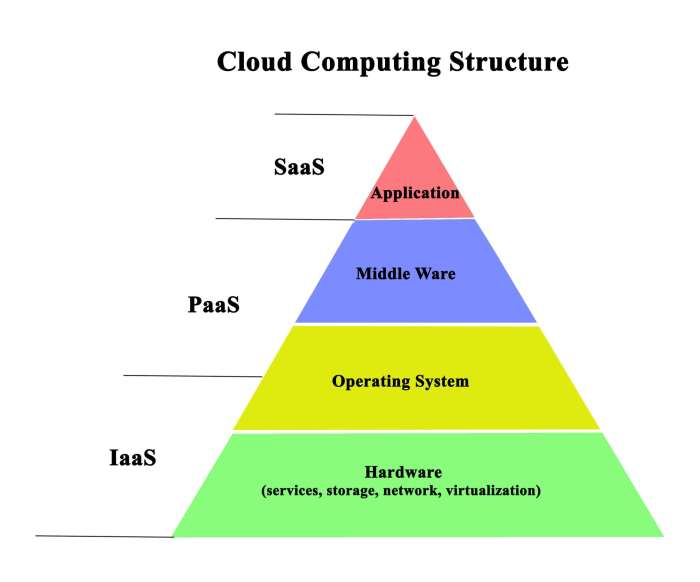
Types of Cloud Computing Models
There are different types of cloud computing models that cater to various business needs:
| Public Cloud | Private Cloud | Hybrid Cloud |
|---|---|---|
| Accessible to the public, cost-effective, and managed by third-party providers. | Dedicated to a single organization, offers enhanced security and control over data. | Combines public and private clouds, providing flexibility and customization options. |
Implementation of Cloud Computing Systems
Implementing cloud computing systems in a business environment can bring numerous benefits, such as increased flexibility, scalability, and cost-efficiency. However, it is essential to follow best practices to ensure a successful transition to the cloud.
Best Practices for Implementing Cloud Computing Systems
- Conduct a thorough assessment of your current IT infrastructure and determine which applications and workloads are suitable for migration to the cloud.
- Choose a reliable cloud service provider that aligns with your business needs and offers the necessary security measures to protect your data.
- Develop a comprehensive migration plan that includes timelines, resource allocation, and risk management strategies.
- Train your employees on how to use cloud computing services effectively and ensure they understand the benefits and potential challenges.
- Monitor and optimize your cloud resources regularly to ensure cost-effectiveness and performance efficiency.
Challenges and Considerations when Migrating to Cloud Computing
- Security concerns: Ensuring data privacy and protection when moving sensitive information to the cloud.
- Compliance issues: Meeting regulatory requirements and industry standards while operating in a cloud environment.
- Integration complexity: Integrating existing systems and applications with cloud services without disruptions.
- Cost management: Balancing the cost of cloud services with the value they bring to the organization.
- Vendor lock-in: Avoiding dependency on a single cloud provider by implementing multi-cloud strategies.
Optimizing Resources with Cloud Computing Services
- Scalability: Easily scale resources up or down based on demand, eliminating the need for overprovisioning.
- Cost savings: Pay only for the resources you use, reducing upfront capital expenses and operational costs.
- Improved collaboration: Enable real-time collaboration and communication among teams regardless of location.
- Enhanced flexibility: Access applications and data from any device, anywhere, promoting remote work and flexibility.
- Disaster recovery: Implement robust backup and recovery solutions to protect data and ensure business continuity.
Mobile Computing in Cloud Systems
Mobile devices play a crucial role in accessing cloud computing systems for businesses, providing users with the flexibility to work from anywhere at any time. Let’s explore the significance of mobile compatibility in cloud applications and the security measures required for a seamless experience.
Role of Mobile Devices in Cloud Access
- Mobile devices allow employees to access cloud-based applications and data on-the-go, increasing productivity and efficiency.
- With mobile access, businesses can stay connected with their workforce and clients, enabling real-time collaboration and decision-making.
- Employees can work remotely using their smartphones or tablets, accessing files and applications stored in the cloud without the need for specific physical hardware.
Importance of Mobile Compatibility in Cloud Applications
- Mobile compatibility ensures that cloud applications can be accessed seamlessly across various devices and operating systems, enhancing user experience.
- Businesses can leverage mobile devices to provide employees with access to critical business tools and information, promoting flexibility and agility.
- Mobile-friendly cloud applications enable employees to work efficiently from different locations or while traveling, improving overall productivity.
Security Measures for Mobile Devices in Cloud Systems
- Implementing strong authentication methods, such as biometric recognition or two-factor authentication, enhances the security of mobile devices when accessing cloud systems.
- Regularly updating mobile device software and applications helps mitigate security vulnerabilities and ensures data protection in cloud environments.
- Encrypting data transmitted between mobile devices and cloud servers adds an extra layer of security to prevent unauthorized access or data breaches.
Programming for Cloud Computing
Cloud computing has revolutionized the way applications are developed and deployed. Here, we will explore the programming languages commonly used in developing applications for cloud computing, the importance of scalability and flexibility in cloud-based programming, and share best practices for designing and deploying applications on cloud platforms.
Commonly Used Programming Languages
When it comes to developing applications for cloud computing, several programming languages are commonly used. Some of the popular languages include:
- Java: Known for its portability and scalability, Java is widely used for building cloud-based applications.
- Python: With its simplicity and readability, Python is a favorite choice for cloud development, especially for data analysis and machine learning applications.
- JavaScript: Often used for developing interactive web applications, JavaScript is also utilized in cloud computing for frontend and backend development.
- C#: Commonly used in the Microsoft ecosystem, C# is preferred for building applications on the Azure cloud platform.
Importance of Scalability and Flexibility
Scalability and flexibility are crucial aspects of cloud-based programming. Applications deployed in the cloud need to be able to scale seamlessly based on demand and adapt to changing requirements. It is essential to design applications that can handle varying workloads efficiently and effectively utilize cloud resources. By incorporating scalability and flexibility into the design and architecture of cloud applications, businesses can ensure optimal performance and cost-effectiveness.
Best Practices for Designing and Deploying Applications on Cloud Platforms
Designing and deploying applications on cloud platforms require careful planning and adherence to best practices. Some key recommendations include:
- Utilize microservices architecture: Break down applications into smaller, independent services to improve scalability and maintainability.
- Implement automated testing and deployment: Use continuous integration and continuous deployment (CI/CD) pipelines to streamline development processes and ensure quality.
- Monitor performance and security: Implement monitoring tools to track the performance of applications and ensure data security in the cloud environment.
- Optimize cost management: Use cloud cost management tools to monitor and optimize resource usage, ensuring cost efficiency in cloud deployments.
Security in Cloud Computing
Cloud computing systems for businesses offer numerous benefits, but they also come with inherent security risks. It is crucial for organizations to understand and address these threats effectively to safeguard their data and operations.
Common Security Threats in Cloud Computing
- Data Breaches: Unauthorized access to sensitive information stored in the cloud.
- Malware Infections: Viruses and malicious software can compromise system integrity.
- Insider Threats: Employees or third parties with access to the system may misuse or leak data.
- DDoS Attacks: Distributed Denial of Service attacks can disrupt cloud services and cause downtime.
Measures and Protocols for Data Security
- Encryption: Data should be encrypted both in transit and at rest to protect it from unauthorized access.
- Access Control: Implement robust authentication mechanisms and restrict access based on roles and permissions.
- Regular Audits: Conduct regular security audits and vulnerability assessments to identify and mitigate risks.
- Backup and Recovery: Maintain regular backups of data to ensure business continuity in case of incidents.
- Compliance Standards: Adhere to industry regulations and standards to ensure data protection and privacy.
Importance of Encryption and Authentication
Encryption plays a critical role in securing data in the cloud by scrambling information to make it unreadable to unauthorized users. Authentication verifies the identity of users and ensures that only authorized individuals can access the system. Together, encryption and authentication form the cornerstone of a robust security framework for cloud-based operations.
Software Applications for Cloud Systems
In today’s digital era, software applications play a crucial role in the functionality and efficiency of cloud computing systems. Let’s explore popular software applications and tools used in cloud computing environments, as well as the benefits of utilizing Software as a Service (SaaS) solutions for businesses.
Popular Software Applications and Tools
- Microsoft Office 365: A well-known suite of productivity tools such as Word, Excel, and PowerPoint, accessible through the cloud for easy collaboration and remote work.
- Salesforce: A cloud-based CRM platform that helps businesses manage customer relationships, sales, and marketing activities efficiently.
- Google Workspace: Formerly G Suite, offers a range of cloud-based productivity tools like Gmail, Google Drive, and Google Docs, promoting seamless communication and collaboration.
Benefits of SaaS Solutions for Businesses
- Cost-Effective: SaaS solutions eliminate the need for businesses to invest in expensive hardware and software licenses, as they can access applications through the cloud on a subscription basis.
- Scalability: Businesses can easily scale up or down their usage of software applications based on their needs, without worrying about infrastructure limitations.
- Automatic Updates: SaaS providers handle software updates and maintenance, ensuring that businesses always have access to the latest features and security patches.
Integration and Customization of Software Applications
- Integration: Businesses can integrate different software applications in the cloud to streamline processes and improve workflow efficiency, such as connecting CRM systems with email marketing tools for better customer engagement.
- Customization: Cloud-based software applications often offer customization options to tailor the functionalities according to the specific requirements of businesses, enhancing user experience and productivity.
Systems Management in Cloud Computing
In cloud computing, system management plays a crucial role in ensuring the smooth operation of cloud systems. System administrators are responsible for overseeing the deployment, maintenance, and monitoring of cloud infrastructure to meet the needs of businesses.
Role of System Administrators
System administrators in cloud computing are tasked with setting up and configuring cloud environments, managing user access and permissions, and troubleshooting any issues that may arise. They are also responsible for ensuring data security, implementing backups, and optimizing system performance.
- Provisioning and configuring virtual machines and resources.
- Monitoring system performance and addressing any bottlenecks.
- Managing storage, networks, and security protocols.
- Implementing disaster recovery plans and backup strategies.
Automation Tools and Processes
Automation tools such as Ansible, Puppet, and Chef are widely used in cloud system management to streamline repetitive tasks, improve efficiency, and reduce human error. These tools help automate the deployment, configuration, and maintenance of cloud infrastructure.
Automation tools enable system administrators to scale their operations and manage large-scale cloud environments more effectively.
Scalability and Monitoring Techniques
Scalability is a critical aspect of cloud system management, allowing businesses to adjust resources based on demand. System administrators employ monitoring tools like Nagios, Zabbix, and Prometheus to track performance metrics, identify issues proactively, and ensure optimal performance in cloud environments.
- Implementing auto-scaling to adjust resources dynamically based on workload.
- Setting up alerts and notifications for system performance monitoring.
- Utilizing load balancing to distribute traffic evenly across servers.
- Performing regular capacity planning to anticipate resource requirements.
Conclusion

As we conclude our journey through Cloud computing systems for businesses, remember that the sky’s the limit when it comes to leveraging this technology for enhanced efficiency and security. Stay tuned for more insights and updates on this evolving landscape!
Essential FAQs
What are the different types of cloud computing models?
Cloud computing models include public, private, and hybrid clouds, each catering to specific business needs.
How can businesses ensure data security in cloud computing systems?
Businesses can enhance data security in cloud systems by implementing encryption, authentication protocols, and regular security audits.





